An open-source data generation platform
Two Six Labs is pleased to introduce Magicwand, an open-source platform to provide high-quality, reliable, and reproducible data sets for Low-and-Slow Distributed Denial of Service (LSDDoS) attacks. Magicwand was developed through DARPA’s Extreme DDoS Defense (XD3) program. We focus on low-and-slow attacks that stealthily degrade server performance through cleverly crafted transmissions of data instead of traditional volumetric DDoS attacks which attempt to overwhelm a server by brute force.
What does Magicwand do?
Magicwand is a Python Command-line interface (CLI) that enables researchers to generate packet capture (PCAP) data with labels for attackers and benign clients. With the use of Docker and JavaScript Object Notation (JSON) files, Magicwand provides a customizable and extensible data generation frame-work to generate a multitude of network traffic PCAPs.
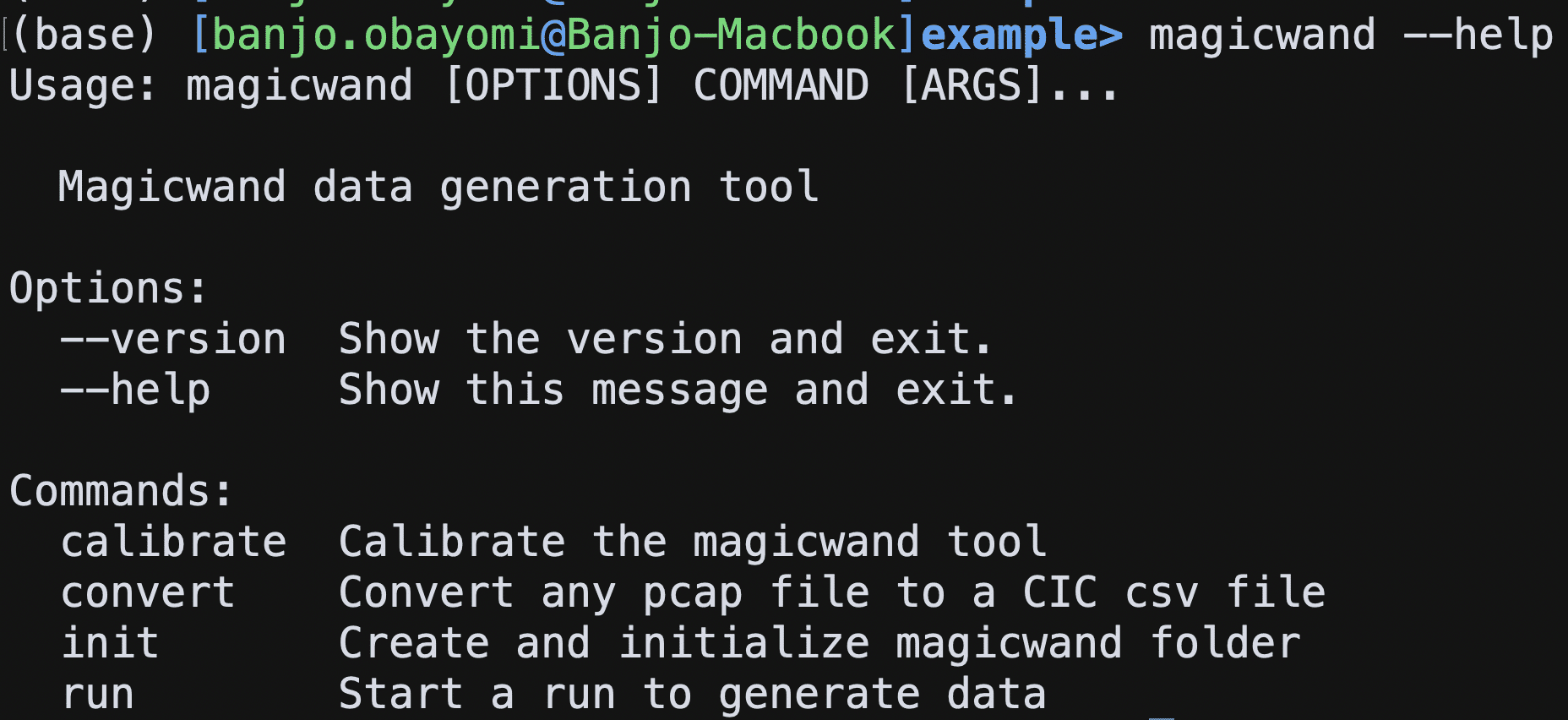
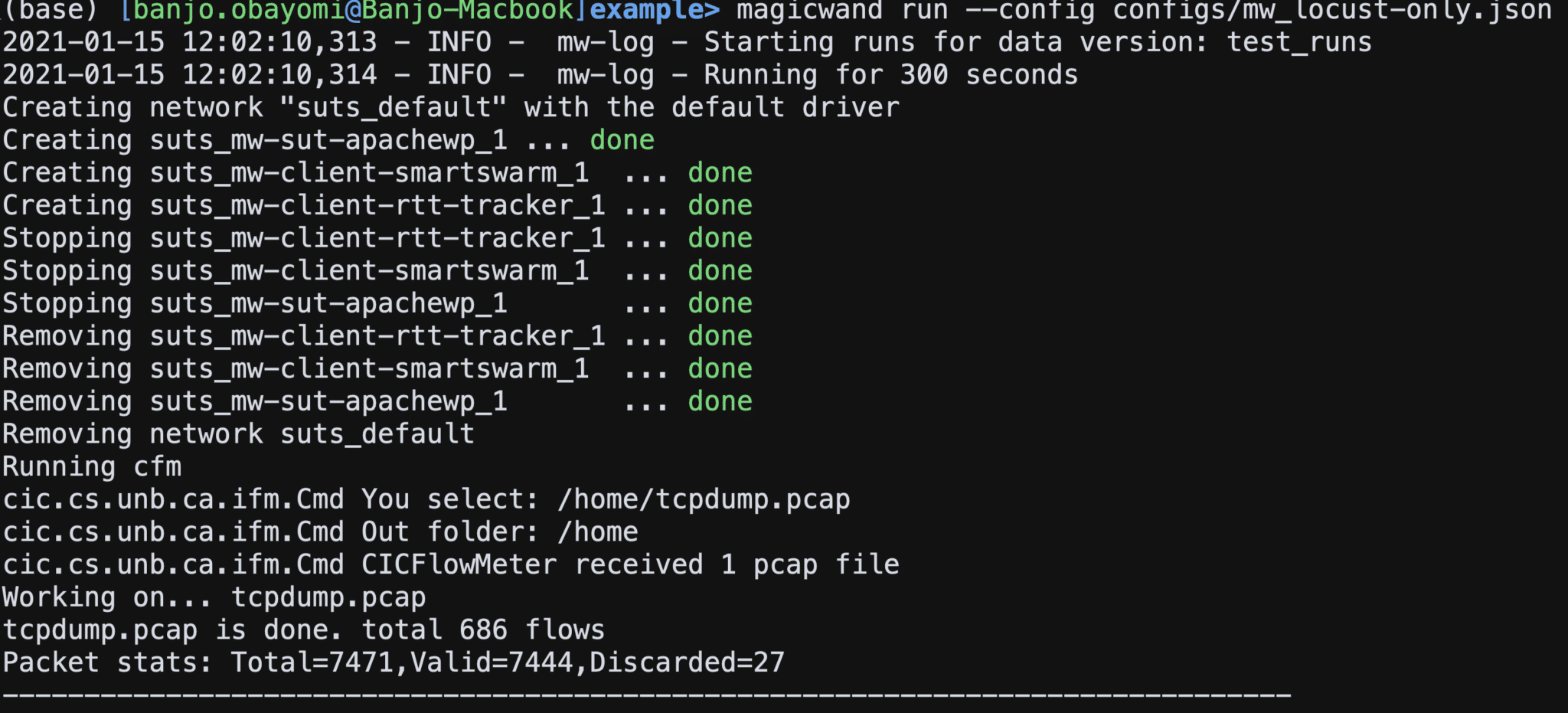
Data is generated by orchestrating configurable experiments with benign and attack traffic targeting a system under test (SUT).
The resulting experiment produces data that includes PCAP data, experiment metadata, the SUT resource/consumption metrics, and more; data is stored locally with machine learning model development in mind.
Why build Magicwand?
Network security datasets are hard to come by due to data privacy concerns. This struggle to capture live traffic and use it for research purposes is limited to very static and unreproducible datasets provided on an ad-hoc basis. To fix the stale dataset problem, Magicwand is a tool to provide researchers with high quality data they can use for network security analysis.
What can you build with Magicwand data?
Magicwand experiments produce raw PCAPs and associated metadata with each run. in addition Magicwand utilizes the FlowMeter tool developed by the Canadian Institute for Cybersecurity. Using Flowmeter each Magicwand experiment creates a CSV with over 80 statistical network traffic features such as Duration, Number of packets, Number of bytes, Length of packets, etc. that can be calculated separately in the forward and backward directions. Magicwand labels each flow as attack or benign giving researchers the ability to develop classifiers that can predict traffic flows based on the network traffic features.
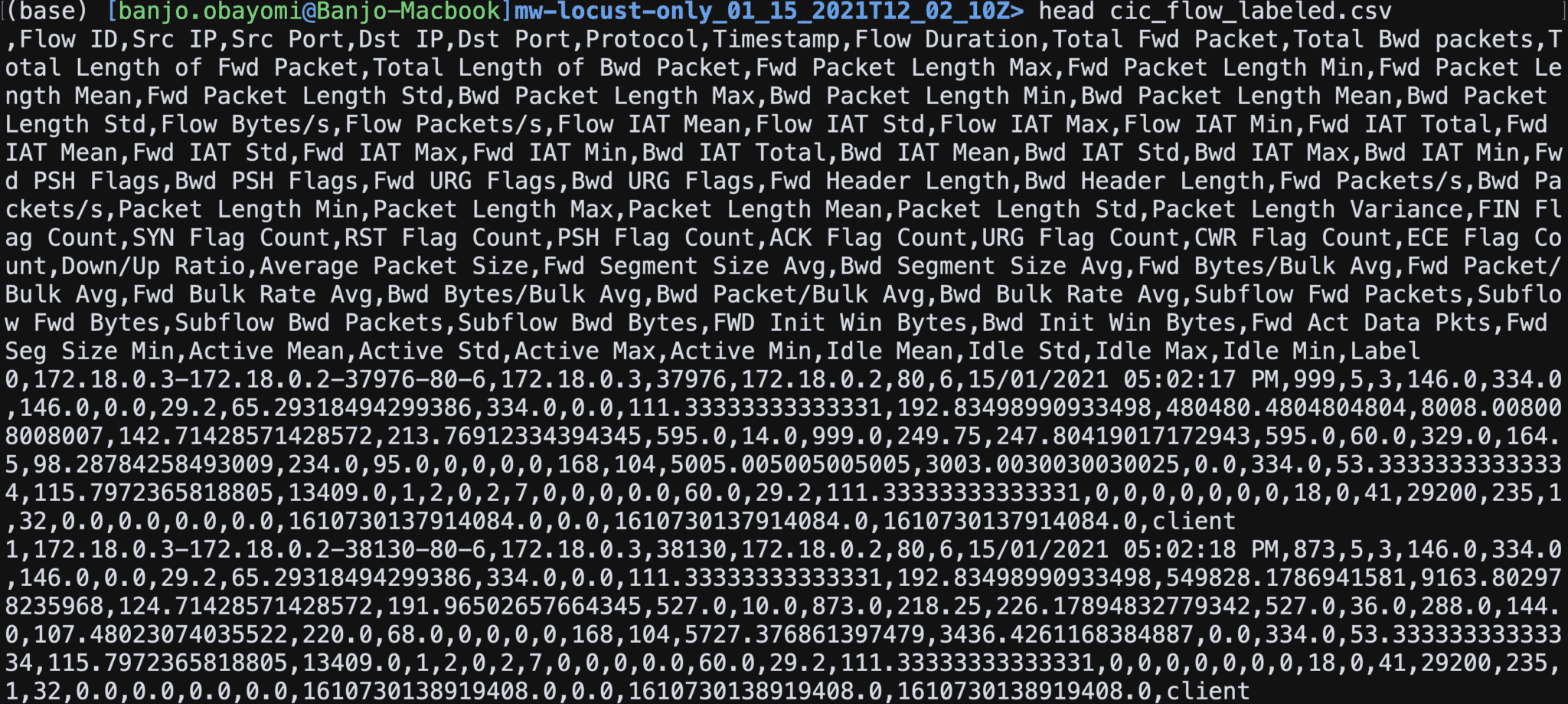
How to use:
You can find the code, and instructions for using the software, on GitHub We welcome bug reports, merge requests, and feature requests, and plan to continue development. If you’re interested in using Magicwand, but think you may need some help, shoot us a message describing your use case and situation at [email protected]. We’re happy to informally provide support as we refine the software’s documentation and make it easier to use.







